3 Ways Content Services & ECM Can Help in Compliance

Presented by: Ephesoft


Presented by: Ephesoft

With the effective date for the new General Data Protection Regulation (GDPR) fast approaching, now is the time to put in a solid strategy when it comes to documents and images. Organizations not only need to implement process and procedure for handling private information, but also need a firm evaluation of “current state” to understand high risk areas of their business and their understand their exposure. Below are the four key steps, as outlined by Microsoft’s GDPR Strategy, and how you can incorporate a document-centric view within your plan:
 Discover
Discover
Discovery will probably be the most challenging step when it comes to documents and GDPR. When it comes to the enterprise, the vast majority have a large number of document repositories. Just think of the modern workplace, and all the locations where documents reside:
The ability to crawl and identify high risk entities within these locations is critical for compliance. Here is a checklist of required functionality when in comes to a technical solution:
 Manage
Manage
Once a GDPR document inventory is complete, and an organization understands their areas of document risk and exposure, a plan can be put in place to manage and govern the assets of their data subjects. This phase or step within your GDPR document strategy can include the following:
 Protect
Protect
In the protection step, organizations need to put security controls on all documents deemed as high risk. But the protection step also requires thought on future documents, and protecting new private assets. As outlined in “Manage”, an effective document transport technology will identify and route newly ingested documents to a protected resting place. Organizations also need to implement real-time controls for high risk identification and classification. Here are some examples:
 Report
Report
The new GDPR standard is all about accurate record keeping, which provides transparency and overall accountability. Knowing all the document types that can be classified as having personal information, and the processes around them, are critical to insure compliance. An audit of policies and procedures is sure to require records of document creation, or ingestion, how it was handled, and where it was ultimately placed under management. All of the technologies mentioned in this article have broad reporting and analytics capabilities.
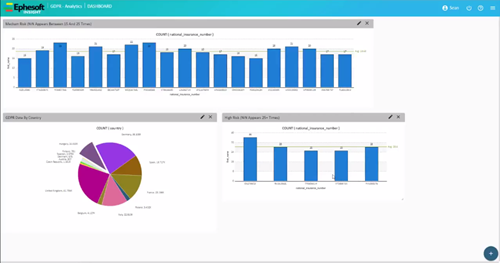
With the complexities of GDPR, standard reporting wont suffice in most cases, and the ability to perform deep analytics to track and identify key data and documents will be a requirement.
Just a quick post on strategy for GDPR when it comes to the unstructured content that lives within documents. Let me know your thoughts on the topic.

As the looming deadline for GDPR approaches, companies are searching for solutions to address numerous challenges. One of the most difficult is historical digital documents. With most large, global organizations having at least 10+ repositories, how can you engage in efficient discovery to find high risk data in the form of documents? This video shows the power of Ephesoft’s GDPR Solution for Documents, Insight.

The new General Data Protection Regulation (GDPR) is set to replace the older Data Protection Directive in the EU on May 25, 2018. This new roll out of privacy protections for EU nations has broad and expansive implications for any company within the realm of the EU, or those that process EU citizen information and data. Here is a summary of the major changes:
 organizations location.
organizations location.There are a set of core subject rights that apply, and below is a quick summary:
So, with that quick outline, imagine the implications of millions of application documents with personal information that are breached. What about the accidental scan of medical records to an insecure document sync folder? Or the directory of millions of scanned documents that have a few documents with private information?
Organizations need a two-pronged approach to prevent the document minefield. So, to get this under control, and mitigate risk, there are really two types of technologies that need to work hand in hand.

First, a document and content capture technology that works as an ingestion point for new content and existing document-centric processes. This form of enterprise input management can be placed as an non-invasive automation layer to flag/identify suspect content and provide reporting capabilities around private information for compliance. Once again, focused on day forward transactions.
Second, is a solution to crawl existing repositories to classify, extract and identify documents that pose a risk. This technology can work hand in hand with the transactional layer to build machine learning profiles, and establish analytical libraries of document and data profiles so the analytical side can become proactive and preemptive. This can be a critical step in identifying possible legacy documents that house private information that could be subject to GDPR fines.
So, where does Ephesoft fit? We have two products that span the transactional and analytical requirements to help organizations capture, classify, identify and visualize their documents in a broad sense, and comply with GDPR privacy rules.
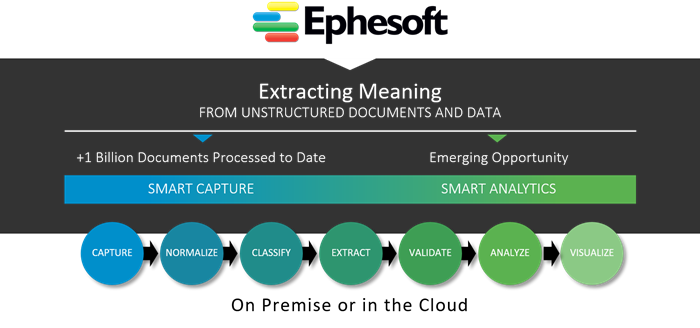
For the day-to-day, we have Ephesoft Transact, and for deep analytics, we have Ephesoft Insight. If you need further information, you can contact us here: Ephesoft GDPR Solution Information.